Table of Contents
1. Getting Started
1.1 Using thermodynamics
1.2 Defining systems
1.3 Describing systems and their behavior
1.4 Measuring mass, length, time, and force
1.5 Specific volume
1.6 Pressure
1.7 Temperature
1.8 Engineering design and analysis
1.9 Methodology for solving thermodynamics problems
1.10 Chapter summary and study guide
1.11 Key engineering concepts
1.12 Key equations
1.13 Exercises: Things engineers think about
1.14 Checking understanding
1.15 Problems: Developing engineering skills
1.16 Design and open-ended problems: Exploring engineering practice
2. Energy and the First Law of Thermodynamics
2.1 Reviewing mechanical concepts of energy
2.2 Broadening our understanding of work
2.3 Broadening our understanding of energy
2.4 Energy transfer by heat
2.5 Energy accounting: energy balance for closed systems
2.6 Energy analysis of cycles
2.7 Energy storage
2.8 Chapter summary and study guide
2.9 Key engineering concepts
2.10 Key equations
2.11 Exercises: Things engineers think about
2.12 Checking understanding
2.13 Problems: Developing engineering skills
2.14 Design and open-ended problems: Exploring engineering practice
3. Evaluating Properties
3.1 Getting started
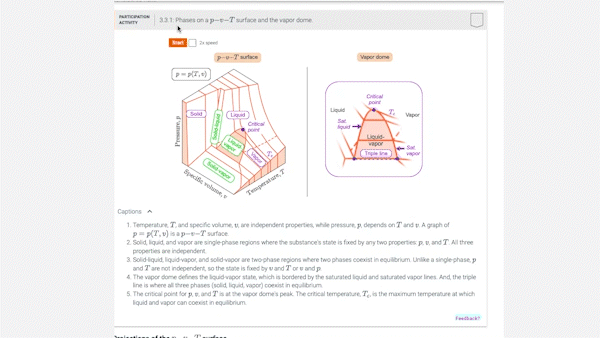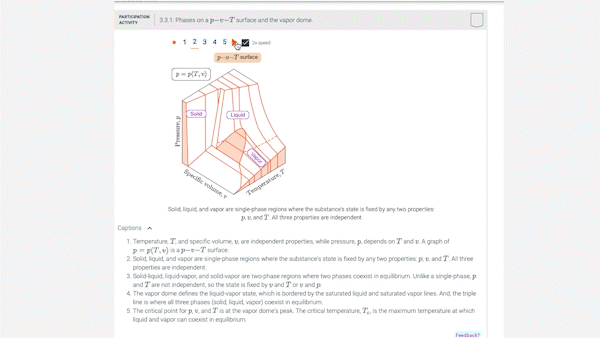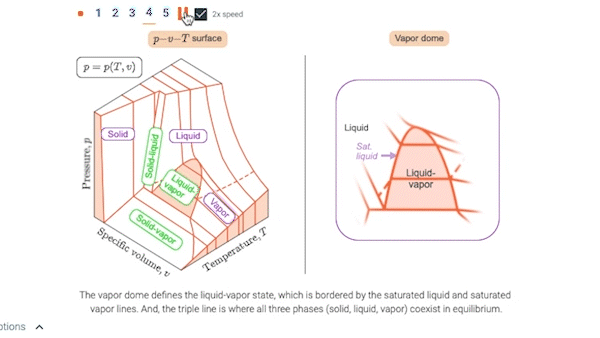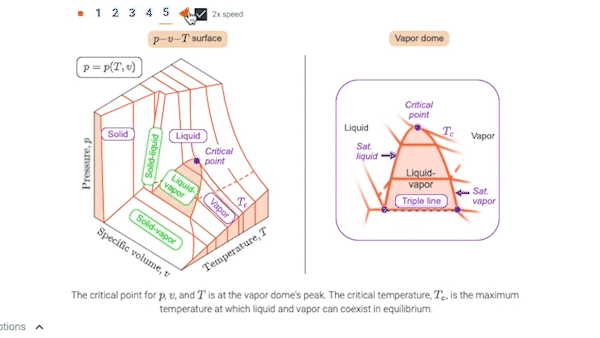
3.2 p-v-T relation
3.3 Studying phase change
3.4 Retrieving thermodynamic properties
3.5 Evaluating pressure, specific volume, and temperature
3.6 Evaluating specific internal energy and enthalpy
3.7 Evaluating properties using computer software
3.8 Applying the energy balance using property tables and software
3.9 Introducing specific heats cv and cp
3.10 Evaluating properties of liquids and solids
3.11 Generalized compressibility chart
3.12 Introducing the ideal gas model
3.13 Internal energy, enthalpy, and specific heats of ideal gases
3.14 Applying the energy balance using ideal gas tables, constant specific heats, and software
3.15 Polytropic process relations
3.16 Chapter summary and study guide
3.17 Key engineering concepts
3.18 Key equations
3.19 Exercises: Things engineers think about
3.20 Checking understanding
3.21 Problems: Developing engineering skills
3.22 Design and open-ended problems: Exploring engineering practice
4. Control Volume Analysis Using Energy
4.1 Conservation of mass for a control volume
4.2 Forms of the mass rate balance
4.3 Applications of the mass rate balance
4.4 Conservation of energy for a control volume
4.5 Analyzing control volumes at steady state
4.6 Nozzles and diffusers
4.7 Turbines
4.8 Compressors and pumps
4.9 Heat exchangers
4.10 Throttling devices
4.11 System integration
4.12 Transient analysis
4.13 Chapter summary and study guide
4.14 Key engineering concepts
4.15 Key equations
4.16 Exercises: Things engineers think about
4.17 Checking understanding
4.18 Problems: Developing engineering skills
4.19 Design & Open-Ended Problems: Exploring Engineering Practice
5. The Second Law of Thermodynamics
5.1 Introducing the second law
5.2 Statements of the second law
5.3 Irreversible and reversible processes
5.4 Interpreting the Kelvin-Planck statement
5.5 Applying the second law to thermodynamic cycles
5.6 Second law aspects of power cycles interacting with two reservoirs
5.7 Second law aspects of refrigeration and heat pump cycles interacting with two reservoirs
5.8 The Kelvin and international temperature scales
5.9 Maximum performance measures for cycles operating between two reservoirs
5.10 Carnot cycle
5.11 Clausius inequality
5.12 Chapter summary and study guide
5.13 Key engineering concepts
5.14 Key equations
5.15 Exercises: Things engineers think about
5.16 Checking understanding
5.17 Problems: Developing engineering skills
5.18 Design & Open-Ended Problems: Exploring Engineering Practice
6. Using Entropy
6.1 Entropy-a system property
6.2 Retrieving entropy data
6.3 Introducing the T dS equations
6.4 Entropy change of an incompressible substance
6.5 Entropy change of an ideal gas
6.6 Entropy change in internally reversible processes of closed systems
6.7 Entropy balance for closed systems
6.8 Directionality of processes
6.9 Entropy rate balance for control volumes
6.10 Rate balances for control volumes at steady state
6.11 Isentropic processes
6.12 Isentropic efficiencies of turbines, nozzles, compressors, and pumps
6.13 Heat transfer and work in internally reversible, steady-state flow processes6.14 Chapter summary and study guide
6.15 Key engineering concepts
6.16 Key equations
6.17 Exercises: Things engineers think about
6.18 Checking understanding
6.19 Problems: Developing engineering skills
6.20 Design and open-ended problems: Exploring engineering practice
7. Exergy Analysis
7.1 Introducing exergy
7.2 Conceptualizing exergy
7.3 Exergy of a system
7.4 Closed system exergy balance
7.5 Exergy rate balance for control volumes at steady state
7.6 Exergetic (second law) efficiency
7.7 Thermoeconomics
7.8 Chapter summary and study guide
7.9 Key engineering concepts
7.10 Key equations
7.11 Exercises: Things engineers think about
7.12 Checking understanding
7.13 Problems: Developing engineering skills
7.14 Design and open-ended problems: Exploring engineering practice
8. Vapor Power Systems
8.1 Introducing vapor power plants
8.2 The Rankine cycle
8.3 Improving performance—superheat, reheat, and supercritical
8.4 Improving performance—regenerative vapor power cycle
8.5 Other vapor power cycle aspects
8.6 Case study: exergy accounting of a vapor power plant
8.7 Chapter summary and study guide
8.8 Key engineering concepts
8.9 Key equations
8.10 Exercises: Things engineers think about
8.11 Checking understanding
8.12 Problems: Developing engineering skills
8.13 Design and open-ended problems: Exploring engineering practice
9. Gas Power Systems
9.1 Introducing engine terminology
9.2 Air-standard Otto cycle
9.3 Air-standard diesel cycle
9.4 Air-standard dual cycle
9.5 Modeling gas turbine power plants
9.6 Air-standard Brayton cycle
9.7 Regenerative gas turbines
9.8 Regenerative gas turbines with reheat and intercooling
9.9 Gas turbine-based combined cycles
9.10 Integrated gasification combined-cycle power plants
9.11 Gas turbines for aircraft propulsion
9.12 Compressible flow preliminaries
9.13 Analyzing one-dimensional steady flow in nozzles and diffusers
9.14 Flow in nozzles and diffusers of ideal gases with constant specific heats
9.15 Chapter summary and study guide
9.16 Key engineering concepts
9.17 Key equations
9.18 Exercises: Things engineers think about
9.19 Checking understanding
9.20 Problems: Developing engineering skills
9.21 Design and open-ended problems: Exploring engineering practice
10. Refrigeration and Heat Pump Systems
10.1 Vapor refrigeration systems
10.2 Analyzing vapor-compression refrigeration systems
10.3 Selecting refrigerants
10.4 Other vapor-compression applications
10.5 Absorption refrigeration
10.6 Heat pump systems
10.7 Gas refrigeration systems
10.8 Chapter summary and study guide
10.9 Key engineering concepts
10.10 Key equations
10.11 Exercises: Things engineers think about
10.12 Checking understanding
10.13 Problems: Developing engineering skills
10.14 Design and open-ended problems: Exploring engineering practice
11. Thermodynamic Relations
11.1 Using equations of state
11.2 Important mathematical relations
11.3 Developing property relations
11.4 Evaluating changes in entropy, internal energy, and enthalpy
11.5 Other thermodynamic relations
11.6 Constructing tables of thermodynamic properties
11.7 Generalized charts for enthalpy and entropy
11.8 p-v-T relations for gas mixtures
11.9 Analyzing multicomponent systems
11.10 Chapter summary and study guide
11.11 Key engineering concepts
11.12 Key equations
11.13 Exercises: Things engineers think about
11.14 Checking understanding
11.15 Problems: Developing engineering skills
11.16 Design and open-ended problems: Exploring engineering practice
12. Ideal Gas Mixture and Psychrometric Applications
12.1 Describing mixture composition
12.2 Relating p, V, and T for ideal gas mixtures
12.3 Evaluating U, H, S, and specific heats
12.4 Analyzing systems involving mixtures
12.5 Introducing psychrometric principles
12.6 Psychrometers: measuring the wet-bulb and dry-bulb temperatures
12.7 Psychrometric charts
12.8 Analyzing air-conditioning processes
12.9 Cooling towers
12.10 Chapter summary and study guide
12.11 Key engineering concepts
12.12 Key equations
12.13 Exercises: Things engineers think about
12.14 Checking understanding
12.15 Problems: Developing engineering skills
12.16 Design and open-ended problems: Exploring engineering practice
13. Reacting Mixtures and Combustion
13.1 Introducing combustion
13.2 Conservation of energy—reacting systems
13.3 Determining the adiabatic flame temperature
13.4 Fuel cells
13.5 Absolute entropy and the third law of thermodynamics
13.6 Conceptualizing chemical exergy
13.7 Standard chemical exergy
13.8 Applying total exergy
13.9 Chapter summary and study guide
13.10 Key engineering concepts
13.11 Key equations
13.12 Exercises: Things engineers think about
13.13 Problems: Developing engineering skills
13.14 Design and open-ended problems: Exploring engineering practice
14. Chemical and Phase Equilibrium
14.1 Introducing equilibrium criteria
14.2 Equation of reaction equilibrium
14.3 Calculating equilibrium compositions
14.4 Further examples of the use of the equilibrium constant
14.5 Equilibrium between two phases of a pure substance
14.6 Equilibrium of multicomponent, multiphase systems
14.7 Chapter summary and study guide
14.8 Key engineering concepts
14.9 Key equations
14.10 Exercises: Things engineers think about
14.11 Checking understanding
14.12 Problems: Developing engineering skills
14.13 Design and open-ended problems: Exploring engineering practice
15. Appendix to Tables in SI Units
15.1 Appendix to Tables in SI Units
16. Appendix to Tables in English Units
16.1 Appendix to Tables in English units
17. Appendix to Figures and Charts
17.1 Appendix to figures and charts
18. Appendix to Conversion Factors
18.1 Appendix to conversion factors
19. Appendix to Constants
19.1 Appendix to constants
20. Appendix to Symbols
20.1 Appendix to symbols
Same Text, More Action
Based on the 9th edition of Fundamentals of Engineering Thermodynamics, this zyVersion contains the complete text of the original book plus new interactive animations and learning questions to engage the student.
- Over 100 animations, like the one you see below, will help students develop a deeper understanding of concepts by visualizing key processes and phenomena
- Almost 200 learning question sets help students understand topics through incremental steps keeping them engaged and providing thorough explanations of both right and wrong answers
- Participation Activities (a combination of animations and learning questions) allow you to see a student’s activity and grant course points for completion
- Approximately 100 Challenge Activites (“auto-graded homework problems”) provide algorithmic, auto-graded versions of the end-of-chapter problems in the original text
Optional Challenge Activities
As an instructor, you have the ability to mark Challenge Activities as optional, which means you can indicate which Challenge Activities your students need to complete in order to meet your course requirements. Those marked as optional won’t contribute to point totals in reports or assignments.
Read our zyBooks guide to fostering student success in Thermodynamics and Fluids:
What is a zyVersion?
zyVersions are leading print titles converted and adapted to zyBooks’ interactive learning platform, allowing for a quick and easy transition to an engaging digital experience for instructors and students.
zyBooks’ web-native content helps students visualize concepts to learn faster and more effectively than with a traditional textbook.
This zyVersion of Fundamentals of Engineering Thermodynamics (9e) benefits both students and instructors:
- Instructor benefits
- Customize your course by reorganizing existing content, or adding your own content
- Continuous publication model updates your course with the latest content and technologies
- Robust reporting gives you insight into students’ progress, reading and participation
- Student benefits
- Learning questions and other content serve as an interactive form of reading and provide instant feedback
- Concepts come to life through extensive animations embedded into the interactive content
- Save chapters as PDFs to reference material at any time, even after the course has been completed
Authors:
Michael J. Moran, Ph.D.
Professor Emeritus, Mechanical and Aerospace Engineering
Howard N. Shapiro
Professor of Mechanical Engineering, Iowa State University
Daisie D. Boettner
Brigadier General, U.S. Army Retired, Professor Emerita, United States Military Academy, West Point, NY
Margaret B. Bailey, Ph.D.
Senior Faculty Associate to the Provost for ADVANCE, PI and Professor of Mechanical Engineering at Rochester Institute of Technology
Contributors:
Adrian Rodriguez
Content Developer, zyBooks
Jocelyn Bale Glickman
Content Developer, zyBooks
Kevin Wood
Content Developer, zyBooks
Prateek Shekhar
Content Developer, zyBooks